DLL injectors are useful for anyone working with software and (especially) game mods. They help change how programs act. Even though this sounds like a big deal, it’s just a tool used by people who make or test software and by gamers.
A DLL Injector lets one software put its code into another using something called a dynamic-link library, or DLL. In this guide, we’ll explain what a DLL injector is, how it works, and where you can find these tools, especially on GitHub.
Page Contents
What is DLL?
A DLL, or Dynamic Link Library, is a type of file used in Windows to share library functions and procedures. It’s like a toolbox that different programs can use at the same time. This lets programs split their jobs into smaller parts, making them easier to make, load, and run.
DLLs are great because they:
- Let you reuse code. Instead of writing the same stuff over and over, a program can use a DLL that has what it needs.
- Help with modular programming. Developers can make programs that load and run functions as needed.
- Save resources. Many apps can use the same DLL, which helps save your computer’s resources.
Think about using photo editing software that lets you save pictures in different formats. The software might use separate DLLs for each format. So, when you save a photo in a certain format, the software just loads the DLL it needs and does its work.
Also see: How to Run CMD, PowerShell or Regedit as SYSTEM or Trusted in Windows 11
What’s an DLL injection?
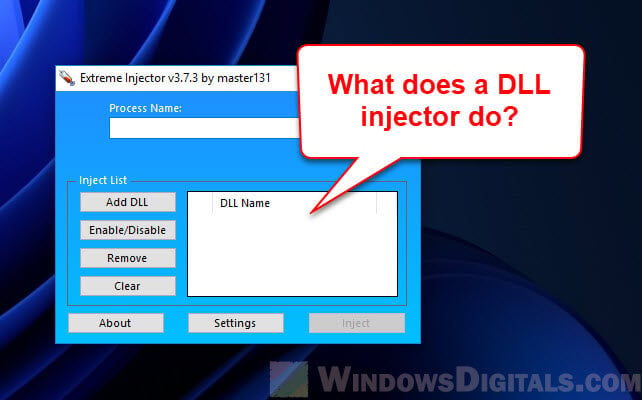
Now that we know about DLLs, let’s talk about DLL injection. It’s a way to put external code, in the form of a DLL, into another program’s space where it runs.
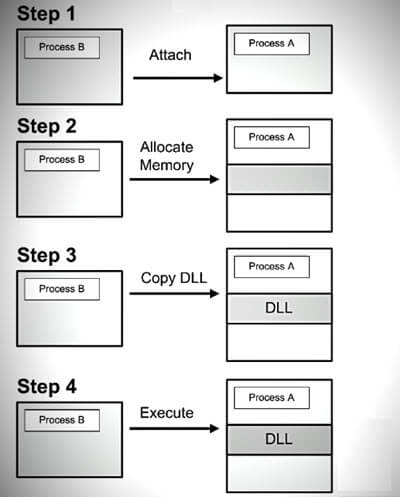
How does DLL injection work?
- The first thing is picking the program you want to inject the DLL into.
- Then, the injector finds space in the program’s memory for the DLL’s path using API functions like
VirtualAllocEx. - Next, the injector writes the DLL’s path into this space using
WriteProcessMemory. - After that, it starts a remote thread in the program that runs
LoadLibrary, which loads the DLL. This is done usingCreateRemoteThread. - Once the DLL is loaded, it starts working right inside the program.
Why use a DLL injector?
DLL injection can be useful for several reasons:
- Developers can put debugging code into apps to find problems and check performance.
- You can add more functions to an app by injecting a DLL.
- Gamers use DLL injection to add new stuff or change things in games. These are what we call modding the games.
- Experts might inject code to see how software works.
- Unfortunately, some people use DLL injection to sneak bad code into good programs, which can hide from security software.
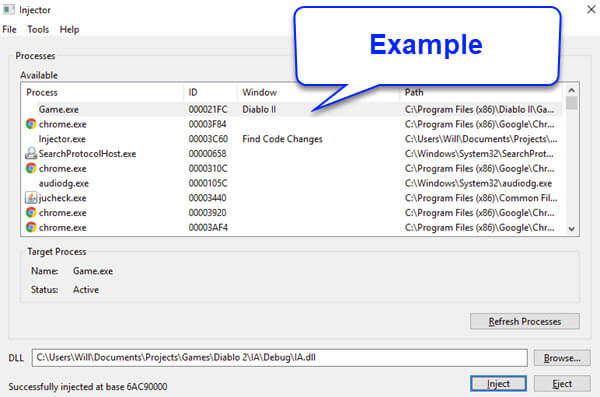
As you can see, DLL injection can be useful but also risky at the same time if used the wrong way.
Related resource: How to Clear RAM Cache in Windows 11
How to find and download DLL injectors from GitHub
Thanks to the open-source community, you can easily find some good DLL injectors on GitHub.
Finding DLL injectors on GitHub
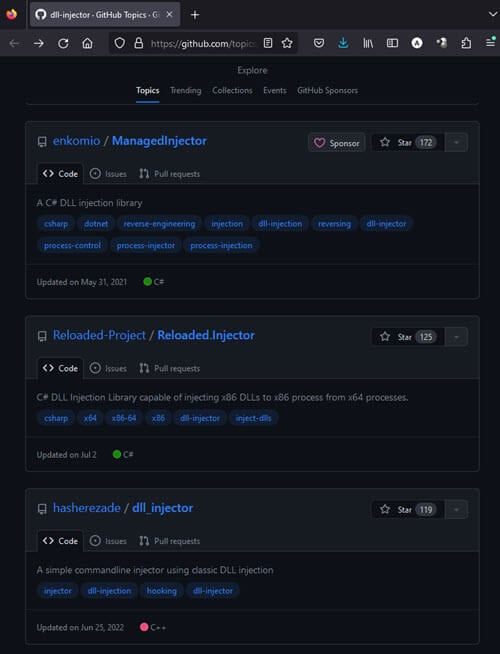
If you’re looking for DLL injectors, GitHub has a special search page just for that.
- Go to the DLL Injector GitHub Topic or search for it on GitHub.
- You’ll see a list of related projects. Each one will tell you a bit about what it does, how popular it is, and when it was last updated.
- When choosing one to download, read its description, check the ratings and comments, and see when it was last updated. Projects that get good reviews and are updated often are usually safer to use.
- Once you pick one, go to its main page and click on the “Code” button to download it as a ZIP file. Make sure to read any instructions to know how to use it right.
- If you have questions or want to help out, you can get involved by posting an “issue” or even contributing to the project.
Although GitHub is a reliable place, the projects are made by users like me and you. Make sure you trust the source, and avoid anything that looks shady or doesn’t have clear instructions.
How to use DLL injectors safely
DLL injection has a lot of good uses, but it can also be misused, which can lead to big security problems.
What could go wrong?
- Bad guys can use DLL injection to sneak malware into legit programs. Once inside, this malware can hide and do bad things like steal data or mess up your computer.
- Malicious DLLs can snoop on data from a program’s memory, which is a privacy no-no.
- Poorly made or evil DLLs can make the program or your whole computer act up or crash.
- Some bad programs can use DLL injection to avoid being caught by normal security software.

What you should do
- Administrators can set rules to only allow trusted DLLs to run.
- Having different levels of trust for processes can prevent less trusted ones from messing with more trusted ones.
- Regular checks with security tools that look for weird behavior can spot problems early.
- Teaching people about the dangers of unknown apps and DLL injection can prevent trouble.
- Using new versions of operating systems helps, as they often have built-in ways to stop unwanted DLL injections.
Also, if you ever need help or have questions about DLL injectors, checking out forums like Reddit should give you more clues and answers.