No matter where you are or what you do, there are always threats around us. And, in the computer world, we are often threatened by something called Trojan virus (I’m sure you’ve heard a ton of times about it). It pretends to be a friendly program but does bad stuff without us knowing. In this post though, we’ll talk about a specific Trojan that caught the attention of many recently called Trojan:Win32/Casdet!rfn. This one targets computers that run on Windows. We’ll cover what it does, how it spreads, and the trouble it can cause.
Also see: Trojan:Win32/Wacatac.H!ml: What You Need to Know
Page Contents
What is Trojan:Win32/Casdet!rfn?
Trojan:Win32/Casdet!rfn, like its name suggests, it’s a kind of malware called Trojan which targets Windows computers and can steal your private info, download more harmful stuff behind your back, or just let hackers get into your computer remotely. It can sneak onto your PC through things like email attachments (often called phishing), bundled software, or bad websites, especially if you don’t have an active antivirus program protecting your system.
This particular Trojan is very good at hiding from antivirus software as well by using rootkits. It makes it super difficult to detect and get rid of.
Similar issue: Removing Survey-smiles.com Malware from Chrome
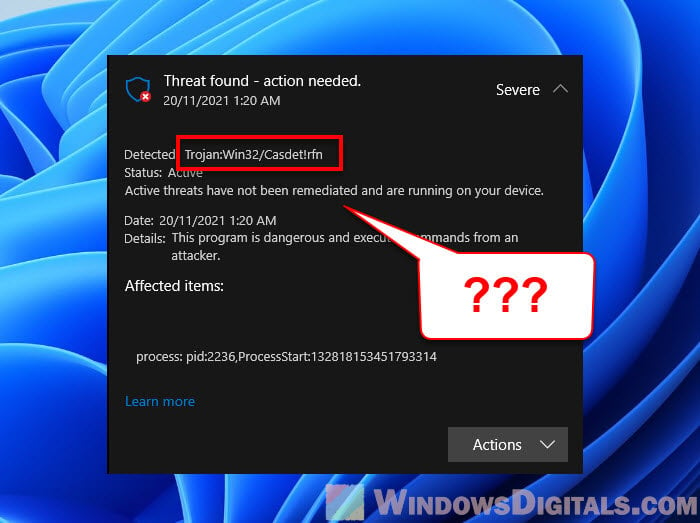
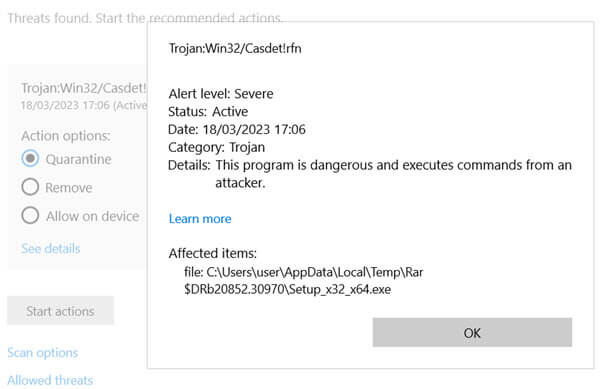
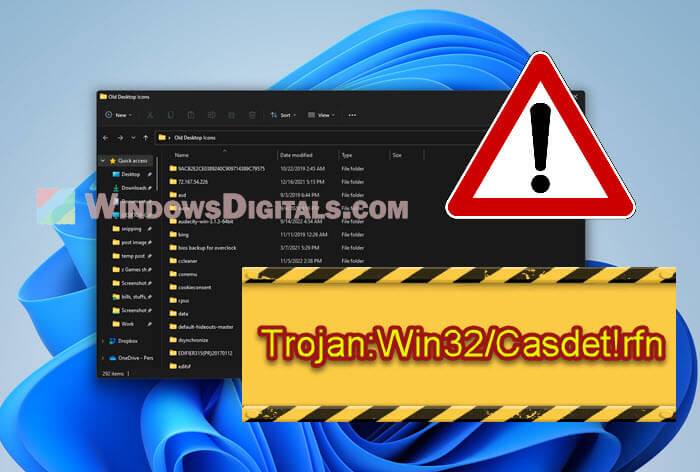
Below is a screenshot showing a warning from Windows Defender about the “Trojan:Win32/Casdet!rfn” virus. This is a heads-up that your computer might be in trouble and you need to do something quickly to get rid of the virus before it’s too late.
How does Trojan:Win32/Casdet!rfn spread?
Trojan:Win32/Casdet!rfn can get around in a bunch of ways, like through email attachments, software that comes bundled together, or iffy websites. Hackers might also try to scare you into thinking your computer has a virus so you download their malware by mistake.
Sometimes, this Trojan comes with other legit software or other viruses, making it hard to spot and remove.
What trouble can Trojan:Win32/Casdet!rfn cause?
- Stealing your private info like passwords, bank details, and personal stuff to use for bad things.
- Downloading more viruses that can mess up your computer even more.
- Letting hackers control your computer from somewhere else.
- Changing how your computer works to keep itself hidden and keep causing trouble.
- Hiding from antivirus programs so it’s hard to find and remove it.
How to remove Trojan:Win32/Casdet!rfn
If you think your computer has caught this Trojan or any other virus, here’s what you should do quickly:
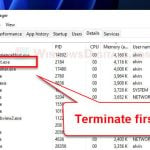
- Get a trustworthy antivirus to find and remove the Trojan:Win32/Casdet!rfn. Keep your antivirus updated and do a full check of your computer. If you don’t have extra antivirus software, Windows Defender (built into Windows) can also do the job. Just make sure to scan your whole computer to catch any bad stuff.
- Get rid of the bad files. Once you find the Trojan, remove any files linked to it. This might include files it put on your computer or files it changed.
- Stop it from coming back. The Trojan might have set up ways to start up again with your computer. Find these tricks and stop them to keep the Trojan from coming back when you restart your computer. You might need to:
- Stop certain programs from starting up with Windows 11
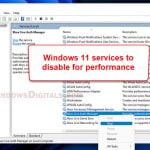
- Turn off certain services from starting up on Windows 11 or 10
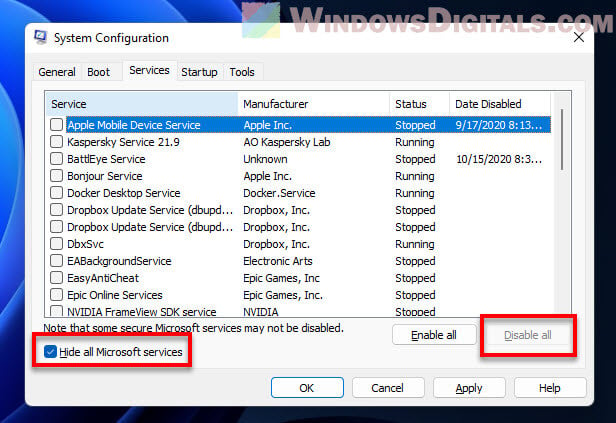
- Fix any settings it changed. The Trojan might have messed with your computer’s settings to keep causing trouble. Look for any changes it made and fix them.
- To avoid getting viruses in the future, keep your computer’s software up to date, use a good antivirus program, and be careful with what you download or open, especially from unknown sources.
Related issue: Windows Defender Security Center Service Missing Windows 11/10
One more thing to note
Be careful with what you click on. Sometimes, even a simple click on a link or opening an email can invite malware like Trojan:Win32/Casdet!rfn into your computer. Always double-check links and email senders to make sure they are from a trusted source before you click.
Too long: didn’t read
To make things short, Trojan:Win32/Casdet!rfn can a big risk to your computer that you should never ignore. It can cause a lot of problems for you and your computer. Double check that your computer is using an up to date and reputable antivirus software, actively protecting your PC from such threats. Be super careful what webpages you open, what items you download, what emails you read, to prevent falling into the traps of cybercriminals.